Penetration Testing
Penetration testing, or pen testing for short, is a method of assessing security by mimicking real-world attacks. It is an iterative process that leverages minimal access to gain greater access. Pentesting will usually fall within one of these categories: Black Box, Grey Box, White Box.
The main difference between these types tests is the amount of information that is provided to us prior to and during the assessment.
During a Black Box test, very little information is provided to us regarding the infrastructure, network, or applications being assessed. This type of test simulates an attack perpetrated by an outsider and is often done as an external test. On the other hand, during a White Box test, a significant amount of disclosure is provided to us. It simulates an attack from and insider such as an employee, contractor, or business partner and is often done as an internal test. Between these two extremes are Grey Box tests.
These are particular useful if a company has a specific area of concern that they would like to make the focus of the assessment. External security testing is conducted from outside the organization's security perimeter.
This offers the ability to view the environment's security posture as it appears outside the security perimeter, usually as seen from the Internet, with the goal of revealing vulnerabilities that could be exploited by an external attacker.
For internal security testing, assessors work from the internal network and assume the identity of a trusted insider or an attacker who has penetrated the perimeter defenses. This kind of testing can reveal vulnerabilities that could be exploited, and demonstrates the potential damage this type of attacker could cause. Internal security testing also focuses on system-level security and configuration, including application and service configuration, authentication, access control, and system hardening.
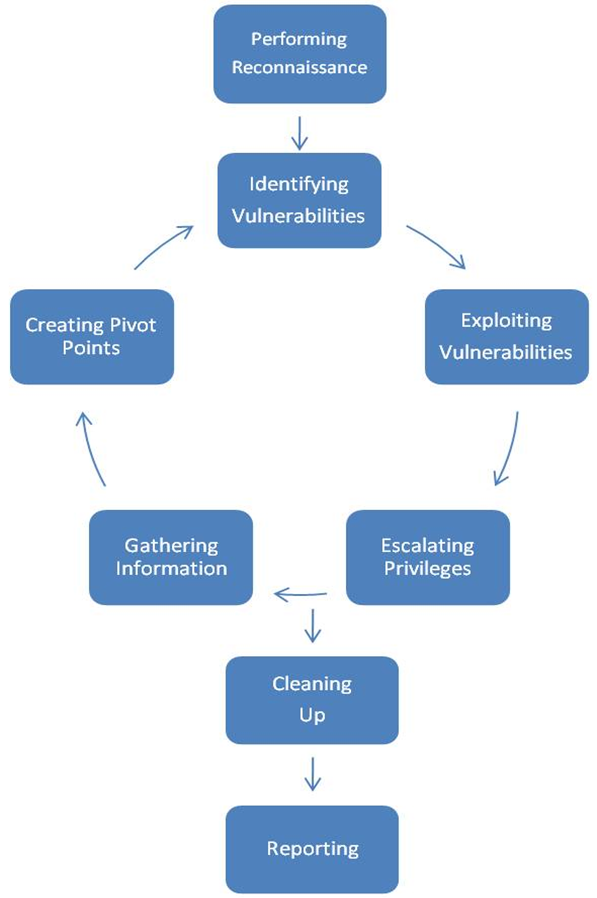
To reduce costs to you we are able to perform both external and internal penetration tests without putting consultants on site. We are able to do this through either VPN connections provided by you or a virtual pentest appliance provided by us. Discovered issues are reported along with and assessment of their risk and recommendations for remediation. Areas of focus: network, web application, and social engineering. Our overall methodology as depicted below is based on NIST's SP800-115. Our web application testing methodology is based on OWASP.
- Resistance to real world-style attacks
- Level of sophistication required to compromise systems
- Countermeasures that mitigate risk
- Attack detection and incident response
Our penetration tests are performed by senior security personnel certified by EC Council, (ISC)^2, ISACA, PCI SSC, and CompTIA.



